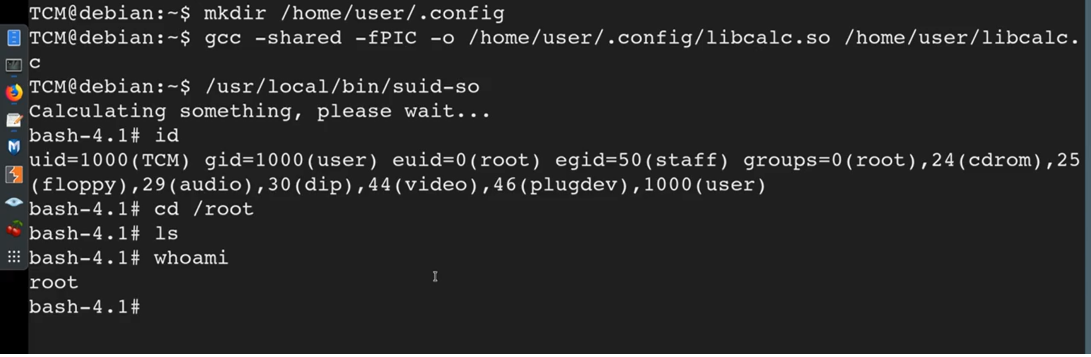
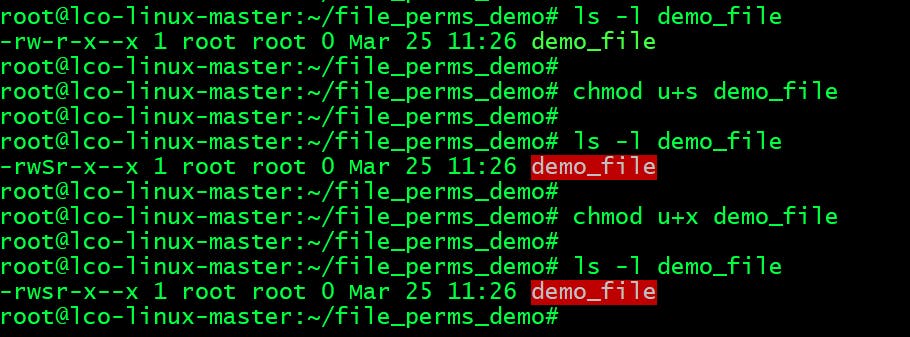
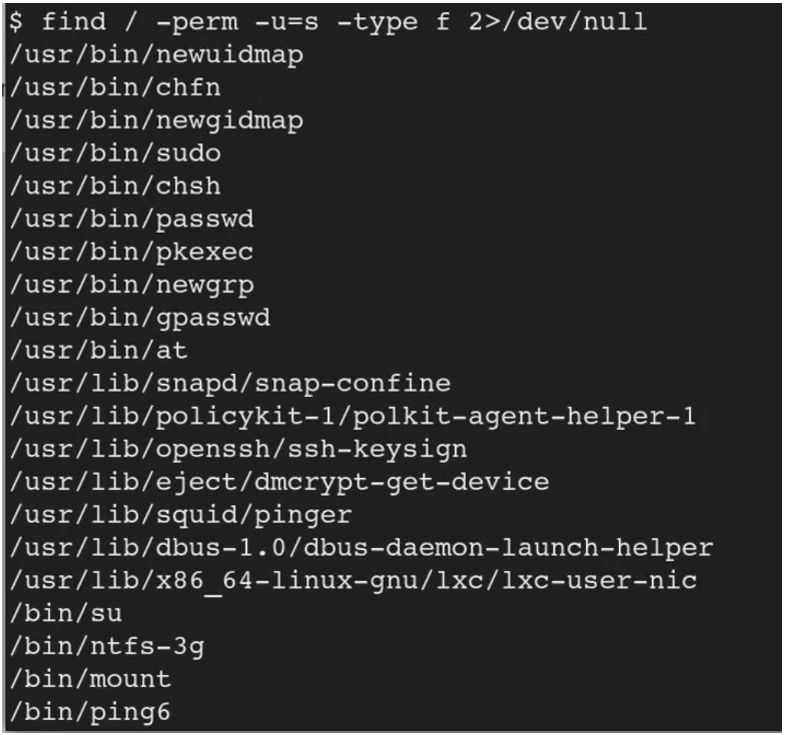
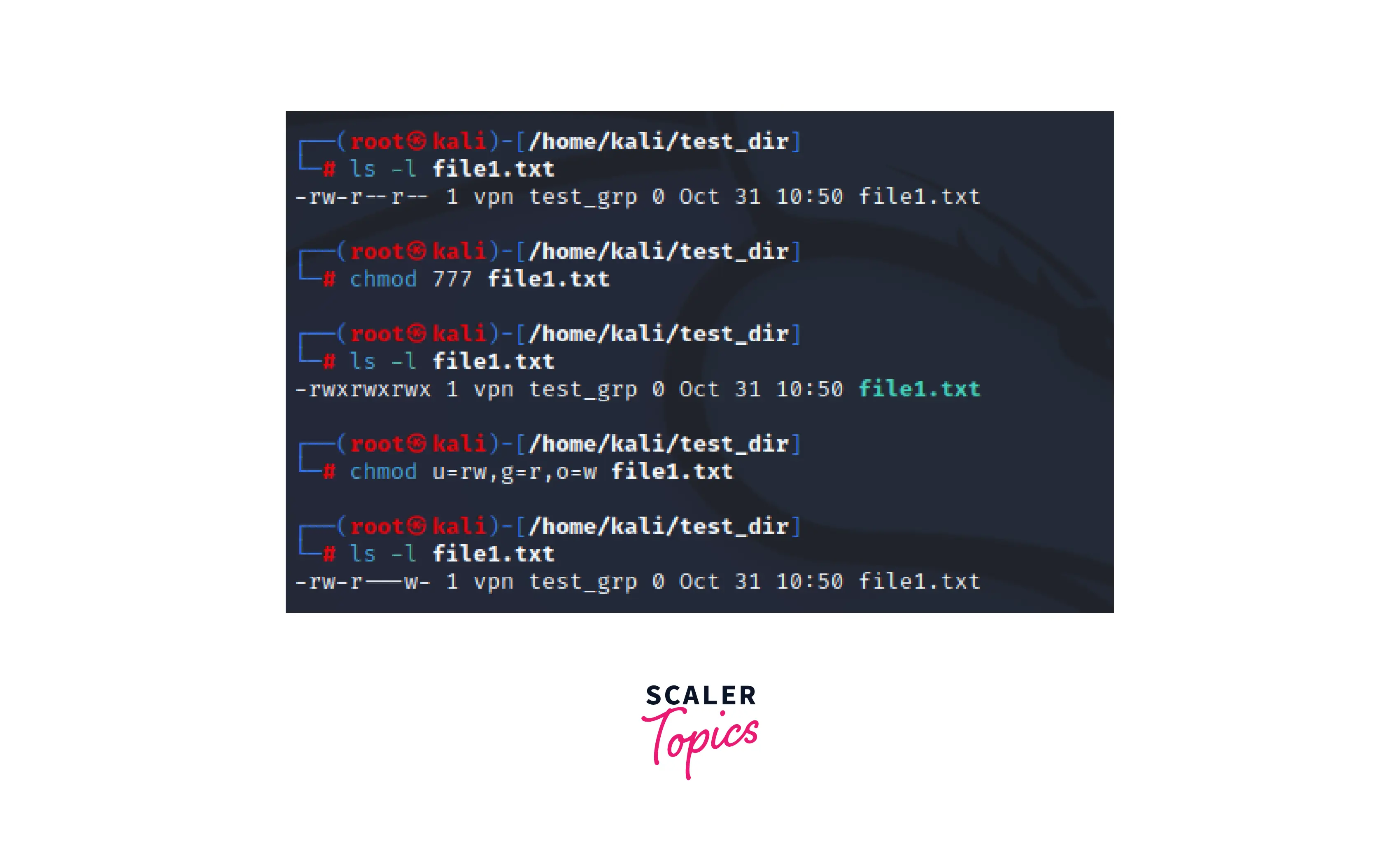
Foundation Topics: Exploiting Local Host Vulnerabilities | Exploiting Local Host and Physical Security Vulnerabilities | Pearson IT Certification
Being a multi-user system - UNIX and Linux have a tremendous amount of security to offer; many being open source, which can be validated and modified. - ppt download
Why would using chmod 777 recursively from the root cause a Linux box to not boot? I could understand this if I were limiting permissions, but why would adding permissions cause this? -
Why is the default file permission 666 in Linux? How is the security effect if the file becomes executable? - Quora
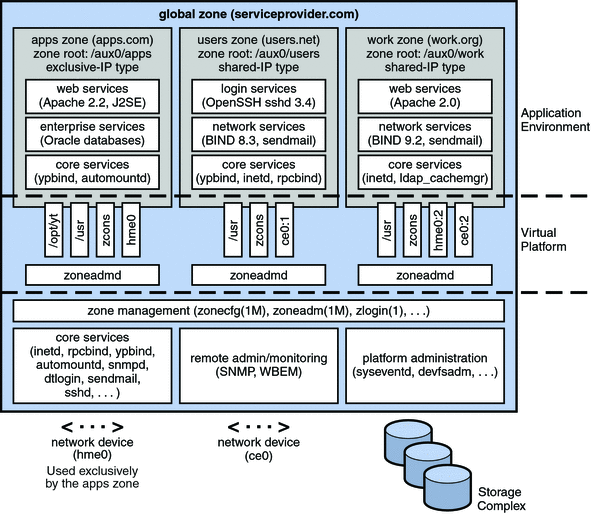
Part II Zones (System Administration Guide: Oracle Solaris Containers-Resource Management and Oracle Solaris Zones)