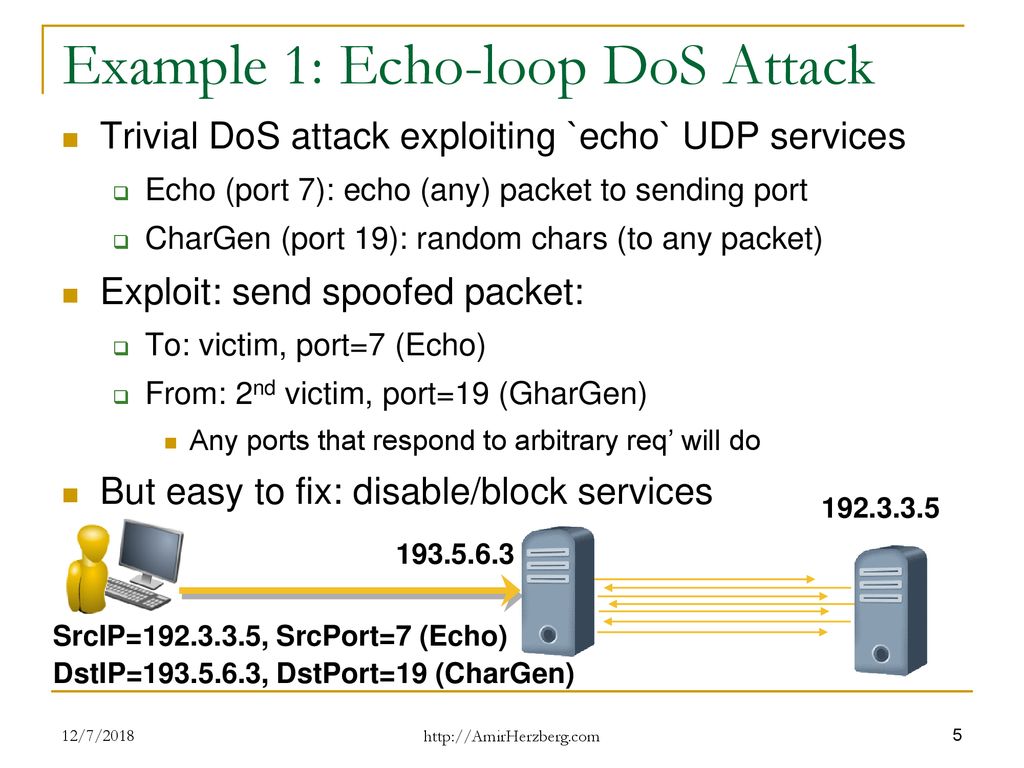
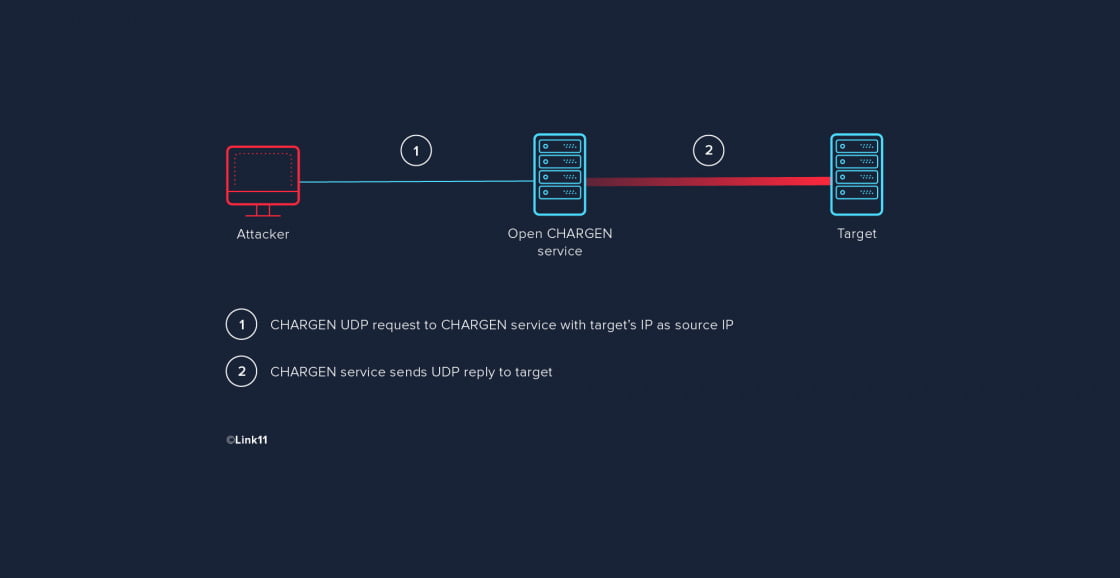
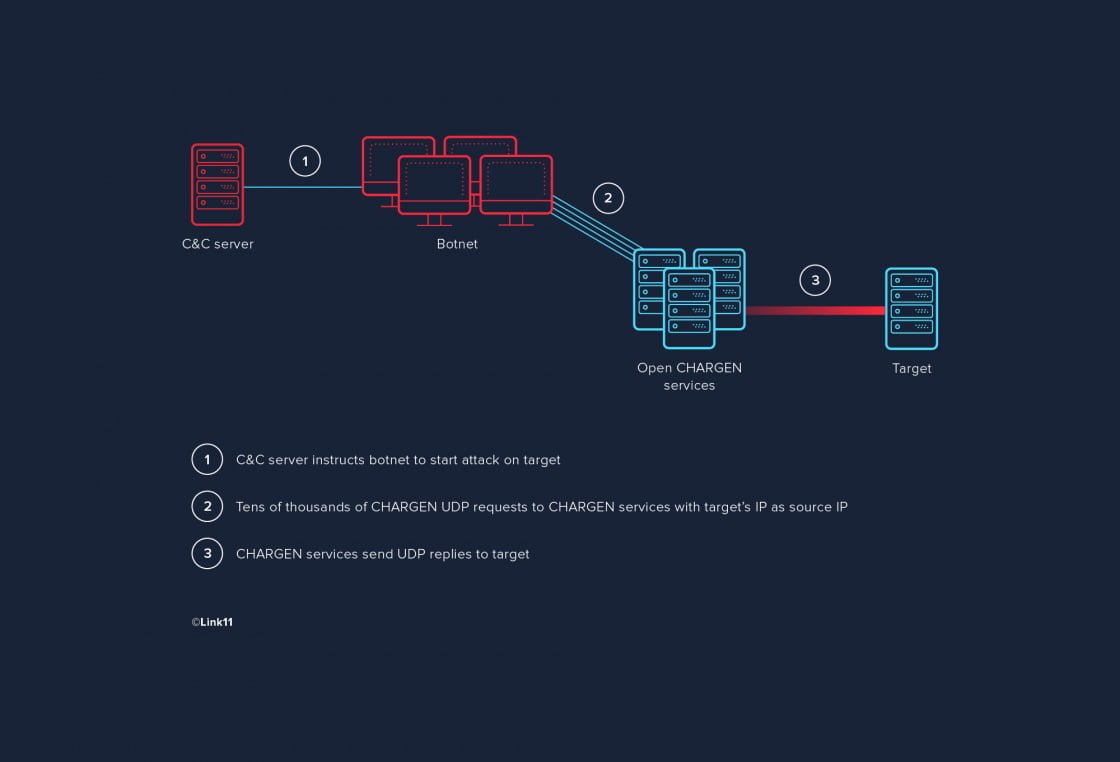
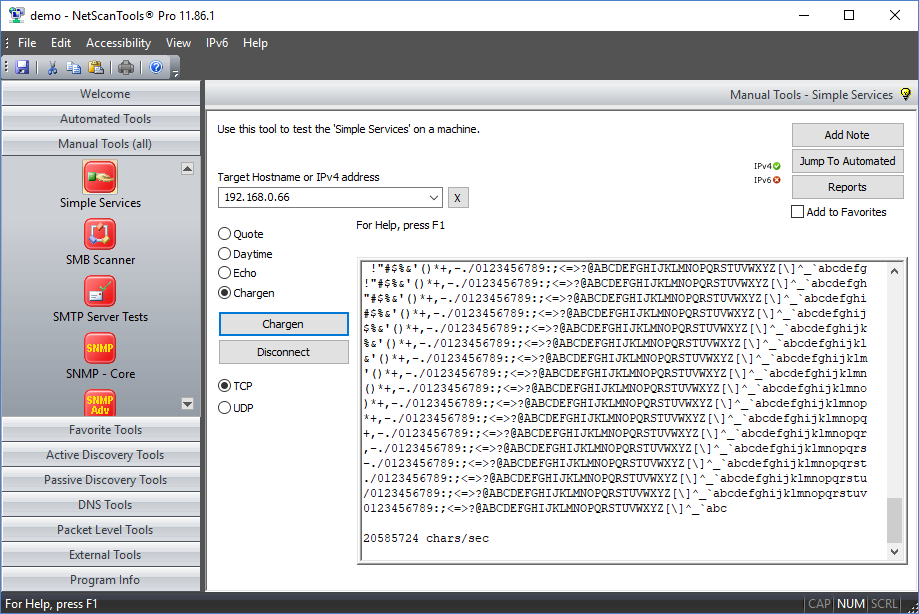
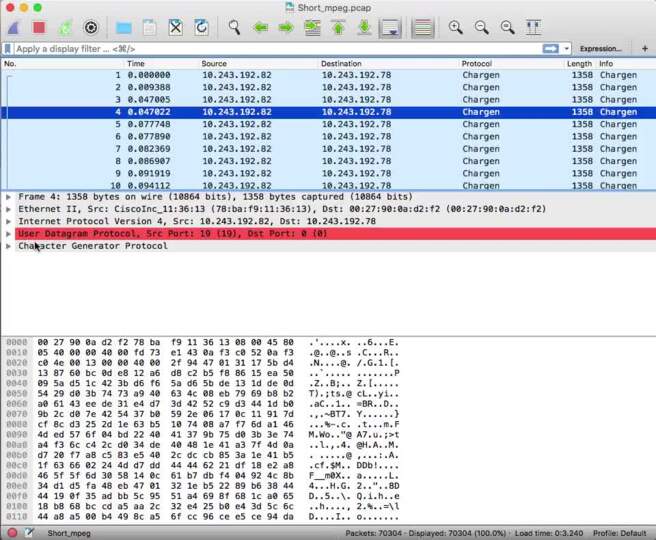
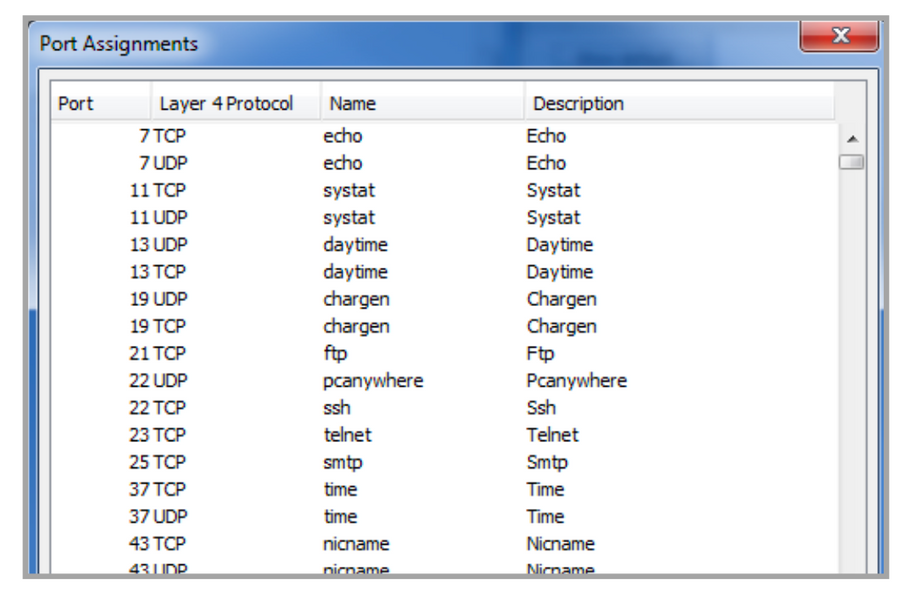
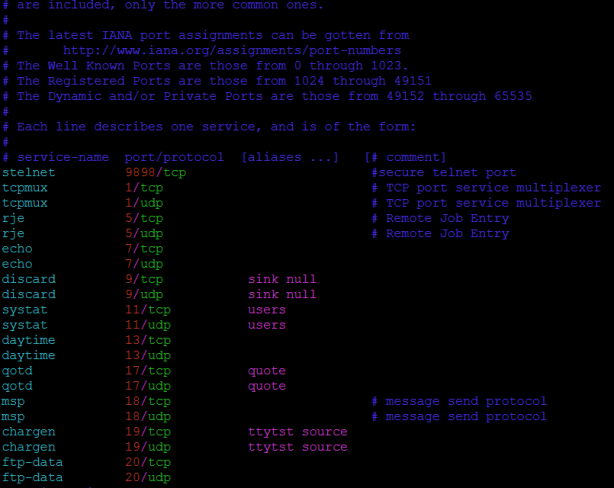
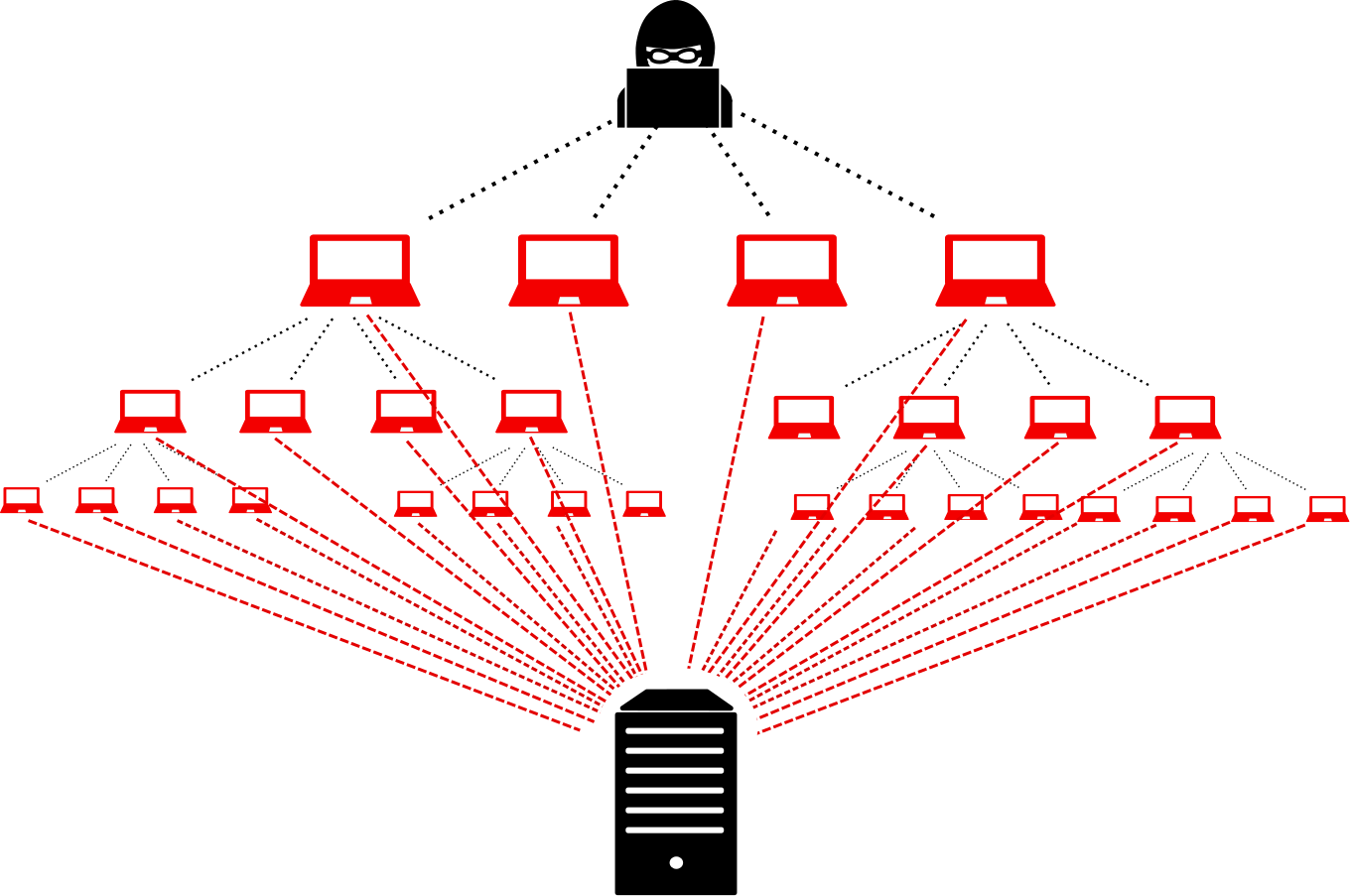
1 CHAPTER 3 CLASSES OF ATTACK. 2 Denial of Service (DoS) Takes place when availability to resource is intentionally blocked or degraded Takes place when. - ppt download

USB Charging Port For LG Nexus 5 D820 D821 Durable Charging USB Port Dock Connector Mic Flex Cable|Mobile Phone Flex Cables| - AliExpress